 Who hasn’t heard of them? And if you have experienced what they are, who can forget such a profoundly frustrating experience?
Who hasn’t heard of them? And if you have experienced what they are, who can forget such a profoundly frustrating experience?
Computer viruses are merely computer programs, designed to self-replicate. They are designed to “infect” other executable programs, by copying the virus code into them. When these infected programs are executed, the virus gets another chance to attack, and will probably try to infect some more uninfected programs, thereby causing some kind of a chain reaction. The virus code remains in memory even after the program terminates, in order to fulfill it’s goal of more infection! As the infected program is copied and used on other uninfected systems, the virus spreads on that system too, infecting many files there.
Contrary to popular perception, viruses need not cause any harm or damage to the computer or the files and data stored there! The definition of a computer virus is just limited to the fact that it is a self-replicating program – the definition does not include it’s activity! While many viruses were written just as an experiment, for fun, or for an ego boost and end up being harmless (though irritating probably), some are written by sadists and have an intended effect of messing up with files and data on the target systems.
The life-cycle of a virus
While the actual behaviour of a virus is completely controlled by the program, and thus the programmer who wrote the program, a general life-cycle exists.
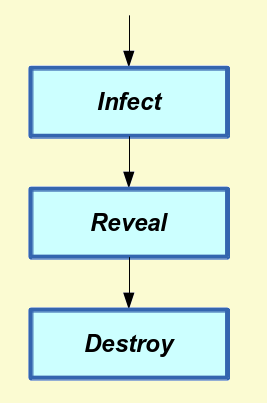 During the first stage, the virus works silently on infecting as many files and computers as possible, and tries to escape detection by striving not to show any signs of infection! If the virus is detected in this stage, some action would normally be taken by the user against it, preventing it’s spread. Hence, it is in the best interest of the virus to not draw any unnecessary attention towards it.
During the first stage, the virus works silently on infecting as many files and computers as possible, and tries to escape detection by striving not to show any signs of infection! If the virus is detected in this stage, some action would normally be taken by the user against it, preventing it’s spread. Hence, it is in the best interest of the virus to not draw any unnecessary attention towards it.
After the virus has spread enough, the second stage sets in. The definition of “spread enough” is given by the programmer who wrote the virus. It could be duration based (n days after the first infection), damage based (after all files that can be infected are infected, or when it finds itself trying to infect an already infected file) or target based (on a Friday that is the 13th day of a month, for example). In this stage, since the virus has already proliferated, it starts showing signs without fear. These indications generally amuse or surprise users at first but can get irritating very soon! Indications include modifying screen contents, generating tones or sounds, displaying messages randomly (sometimes offensive messages), unexplainable disk activity, creation or deletion of files automatically, etc. On older systems, one of the effects of viruses in this stage was to slow down the system drastically – sometimes this was completely unintentional, but was because of multiple copies of the virus in memory. This is the stage in which the virus gains “recognition”.
After the virus has made it’s presence felt, in the last stage it might try to cause some damage! It can delete files, corrupt and overwrite data, format parts of disks and do anything to make your computer unusable or unreliable! It is at this stage that deletion of files does not cause loss of propagation to the virus. Many viruses are non-destructive, and does not do anything in this stage. However, there have been cases of even non-destructive viruses being discovered and modified into destructive viruses by programmers other than the original authors!
My experience with viruses!
On a personal note, my journey with viruses started with the same level of excitement as my journey with computers and programming! My fascination for these made me learn more about them, and deal with them not only in my personal case, but also in the cases of all my classmates, seniors and juniors. Soon enough, I was nicknamed “the computer doctor” – a good name, considering the fact that I could literally touch a computer and find out the presence or absence of viruses! And just before you conclude that I’m getting into the paranormal, here is the technical explanation of it.
 The computers we used back in school did not have hard disks and we used 5.25” floppy disks to boot DOS. The movement of the read-write head on the disk caused vibrations that could be felt by hand. The presence of virus code perhaps altered the regular movement of the read-write head to go to different tracks and sectors in the disk in order to load the virus code. This resulted in a slightly different pattern of vibration, which I used as an indicator to detect the presence of a virus. And I was probably never wrong – a quick scan with an anti-virus software would confirm my claim!
The computers we used back in school did not have hard disks and we used 5.25” floppy disks to boot DOS. The movement of the read-write head on the disk caused vibrations that could be felt by hand. The presence of virus code perhaps altered the regular movement of the read-write head to go to different tracks and sectors in the disk in order to load the virus code. This resulted in a slightly different pattern of vibration, which I used as an indicator to detect the presence of a virus. And I was probably never wrong – a quick scan with an anti-virus software would confirm my claim!
I was quick to understand the threats and mechanisms of viruses, and insisted on “write-protecting” floppy disks generally (those 5.25” disks had a notch that could be covered by a tape to write-protect it, making it impossible for the computer to write any data on to it when in that state). Especially the bootable disks, disks containing anti-virus software or precious pieces of completed work were the ideal candidates for permanent write-protection!
It was fun diagnosing various situations and suggesting remedies and actions, and executing them on confirmation, together with giving words of advice on how to prevent these situations! There were a few who felt that I was being over-protective and paranoid, but these people paid the price by experiencing first-hand how a virus can destroy all that they possess in the electronic world, and became like me in the end!
I showed keen interest in the concept of TSR (Terminate and Stay Resident), the basic hook that all viruses back then had to use in order to stay in memory. I did write a couple of TSR programs myself, but all for constructive reasons – and none of them was a virus!
After shifting over to Linux, I completely lost touch with viruses!
Types of viruses
Viruses are categorised based on the mechanism they use to spread into the system. The first to enter the scene were boot sector viruses, then executable viruses, and finally macro viruses and email viruses.
Boot sector viruses are those viruses that add code into the boot sector. The boot sector is the first sector of a disk, and instructions from here are blindly loaded by the computer when it is booting (the process the computer follows on switching on, in order to load the operating system). Since the boot sector was only a single sector and could contain only that much code, the code in the boot sector normally would contain instructions to load additional code from other sectors. A boot sector virus would insert code into the boot sector that results in the virus code being executed every time the system boots. Neat!
Executable viruses attach themselves to executable files, which ensures that the virus code gets a chance to run everytime that program is executed. However, when the program terminates, the virus can continue to remain in memory using a concept called Terminate and Stay Resident. The virus can then do whatever it wants, whenever it wants, while it is in memory. One of the main things such a virus would do would be to locate other executables and infect them too, if they are not already affected.
Later viruses tried to combine both the approaches for “maximum reach”!
When Microsoft Office documents started becoming more popular and commonplace, and programming support was added into them via VisualBasic Macros, this led to a new programming environment for viruses! Macro viruses were able to harness this to spread the virus code to other office documents.
When emails became popular, programmers started using this virtual connection as a way to spread programs. A virus could easily send spam to any or all contacts, without the knowledge of the sender, with the virus code attached to the mail. Any recipient who receives the mail and runs the executable permits the chain to propagate.
Detection: How do I know if my computer is infected?
 Detection of a virus can be very tricky unless the virus is in the second stage and has already finished a considerable amount of spreading. An anti-virus software can easily scan and detect the presence of various viruses based on it’s database of viruses, however no database can be 100% correct and complete as viruses are continuously being developed and can even “mutate”!
Detection of a virus can be very tricky unless the virus is in the second stage and has already finished a considerable amount of spreading. An anti-virus software can easily scan and detect the presence of various viruses based on it’s database of viruses, however no database can be 100% correct and complete as viruses are continuously being developed and can even “mutate”!
Some signs nevertheless that could hint at the presence of a virus are:
- You see strange messages or error messages that you have never seen before
- Your programs take much longer to run the before
- Your system takes a longer time to boot than before
- Your I/O devices (keyboard, mouse, monitor, printer) do not work as expected
- You see disk activity when you were not expecting it
- Some drives are suddenly inaccessible
- Some files or directories suddenly appear or disappear
- Your system simply hangs or automatically reboots
An anti-virus software is perhaps the most reliable bet at virus detection. However, do note that they still don’t have the final say!
Elimination: What do I do if my computer is infected?
The virus could have done anything. You might have lost precious data and have to track down what you have lost – and probably cannot get back what you have lost. You also will need to find where all it has spread in order to remove it completely from your system and perhaps from your life!
The first thing to do is to seek the refuge of a good anti-virus software, which hopefully will be able to do two things: remove all traces of the virus, and bring back to life all your existing data. The anti-virus software, however, needs a “clean environment” to run and do all these – otherwise the virus can run in parallel with the anti-virus! It is recommended that you boot from a clean disk, and run a clean version of the anti-virus, which itself is guaranteed not to have any viruses!
If you are not that lucky and your anti-virus is unable to remove a virus from a file though it has detected it’s presence, it is wise to delete the file completely so that it cannot cause any further harm. In fact, deletion of all executable programs can get rid of executable viruses, and deletion of all office documents can get rid of macro viruses. Boot sector viruses cannot be manually removed. Do look at hidden files too!
If you can afford to lose all data on the disk, the best solution would be to boot clean and format the contents of the disk.
Prevention: How to prevent virus attacks?
Prevention is better than cure – and I strongly recommend that you don’t even see out of curiosity what havoc a virus can cause in your system!
Here are some tips on how to prevent a virus entering your system in the first place:

- Have a good anti-virus scanner running in the background, monitoring activity on your computer
- Ensure that the database of this anti-virus is up-to-date to even detect the latest viruses and mutations
- In order to safeguard against executable viruses, do not copy (and especially, do not execute) any executable programs from the outside world, no matter how tempting. If this becomes a dire necessity, do a virus scan on that program first before accepting. Also consider the trustworthiness of the program source.
- Do not boot from any other device or disk in order to safeguard against boot sector viruses.
- Disable macro execution in Microsoft Office, and enable on a per file basis only when you trust the source and when it is critically required. This will curb the spread of macro viruses.
- Do not download, execute or activate any link or attachment in an email.
- Switch over to a more secure operating system like Linux. Hardly any viruses exist on Linux!
Anti-Viruses and how they work
If viruses are computer programs designed to torture you, anti-viruses are counter programs designed to detect and eliminate viruses, to recover data and to prevent further incidents of viruses!
 Every virus, being a unique program, has a unique piece of code. Some part of this code is taken as the “signature” of the virus. Anti-virus companies collect “samples” of virus when there is an attack, determine the signature, and add it to their database of known viruses. The anti-virus software can then locate programs that contain such signatures and flag them for presence of the virus.
Every virus, being a unique program, has a unique piece of code. Some part of this code is taken as the “signature” of the virus. Anti-virus companies collect “samples” of virus when there is an attack, determine the signature, and add it to their database of known viruses. The anti-virus software can then locate programs that contain such signatures and flag them for presence of the virus.
There is a well-known piece of advice: don’t use multiple anti-viruses simultaneously on a system. One of the reasons for this is that both compete for memory and processor time, slowing down the machine, and additionally each can potentially flag the other as a virus-containing program since virus signatures are found there!
Once an anti-virus company determines the signature of a virus, that’s the end of the virus as long as this anti-virus is used. That should have been the case, but then virus writers got a bit more intelligent and started writing self-modifying viruses! These viruses change their own code with every infection, making it difficult for anti-virus companies to freeze in on a particular signature. Anti-virus companies started relying on heuristics to counter this! Heuristics means that the anti-virus is no longer dependent on an exact virus signature, but can detect anomalies using any of the following:
- File Emulation: Allow the program to run within a sand box and observe what kinds of requests emerge from it. Anything fishy?
- File Analysis: Go through each instruction in the program and try to figure out whether it does things that viruses usually end up doing. Anything fishy here?
- Generic Signatures: We may not have an exact match of a virus signature, but is there something close to it? It could be a mutant variant!
Heuristics can be powerful, but lack the definiteness. Nevertheless, if an anti-virus says that it’s heuristic scan has yielded positive results, trust it and take the suggested action unless you have a strong reason to disbelieve it!
It is a race out there between virus creators who are looking at innovative ways of spreading their viruses by escaping the anti-viruses, and anti-virus creators who are constantly updating their databases and looking out for newer varieties of more powerful viruses!
Computer Viruses and Biological viruses
The fundamental reason why computer viruses are so called is because of the similarity with biological viruses! While there is no connection between these two, it is fascinating to see the surprising similarities!
| Biological Virus | Computer Virus |
|---|---|
| They spread to other hosts | They spread to other computers |
| They do not re-infect the same cell | They do not re-infect the same file |
| The copying is done by the host cell | The copying is done by the host system |
| They integrate into the DNA of the host cell | They attach to the code of the infected program |
| Host organism does not immediately notice the infection | User does not immediately notice the infection |
| Symptoms arise with time | Symptoms arise with time |
| Can remain dormant, though present | Can remain dormant, though present |
| Infects only specific targets, ignoring the other cells | Infects only specific types of files, ignoring the other file |
| Not every target cell is infected | Not every target file is infected |
| Each virus is specific to a particular host | Each virus is specific to a particular operating system |
| There are different species of viruses, with variants within the species | There are different families of viruses, with variants within a family |
| There are different degrees of virulence | There are different degrees of damage done |
| Some viruses mutate | Some viruses mutate |
| Some viruses are seasonal | Some viruses show up at a specific time |
| Can be identified by their DNA signature | Can be identified by their (code) signature |
| Their DNA sequence is the virus information | Their code is the virus information |
| Immunization is possible with the use of anti-viruses | Immunization is possible with the use of anti-viruses |
Virus FAQ
Why are viruses written?
If viruses are potentially destructive and are never helpful, and if they are programs written by programmers, then why do programmers write them?
A valid question! There could be a couple of reasons:
- Viruses could be written as an amusement, private project, but then gets leaked out (mostly unintentionally) from the lab where it was running as an experiment!
- More commonly, it could be an expression of an ego issue – the fact that your virus is running all over the world could perhaps give you a sense of dominance.
- Finally, there are the sadists, who get their kicks from the suffering and helplessness of poor, innocent souls.
There could be other reasons too. There was an incident where 2 Pakistani brothers invented a virus (called Ashar, also called Brain) to prevent misuse of their software.
Which types of files get infected?
While virus code can potentially be added into any file, it does not make sense to add them into files where they have no effect. Thus, the following kinds of files are generally spared:
- Audio files (mp3, wav, mid, etc.)
- Video files (avi, wmv, mpg, etc.)
- Image files (bmp, gif, jpg, etc.)
- Data files (txt, xml, dat, etc.)
Files which are prone to infection in Windows are:
- Executable files (.exe and .com)
- Office documents (.doc, .xls, .ppt)
Do anti-virus companies themselves write viruses?
While there hasn’t been any such widely publicised incident, it is possible for anti-virus companies to create and propagate viruses, because
- They already have all the necessary expertise at their disposal as they are dealing with viruses all the time
- They are aware of the problems faced by their anti-virus as new types of viruses emerge and have access to new technologies that viruses use
- They are the most likely ones to ever gain financially because of a virus
That being said, it is not necessary for anti-virus companies to take the risk and invent viruses as viruses are being continually released by independent virus programmers.
Can viruses cause hardware damage?
It is unlikely for a virus to be able to cause direct hardware damage, although not impossible! However, there are many ways a virus can indirectly manage to cause hardware issues. Some examples are:
- In olden days when monitors used a phosphor coating, a pixel being continuously on could cause the phosphor coating to burn out. A virus can easily ensure that specific pixels are always on, thereby burning the phosphor coating there. That technology is obsolete today.
- A virus can ask a disk to spin continuously, which can wear out the motor eventually
- A virus can pass on parameters to hardware that it is not capable of sustaining for long periods of time
Is it wrong for me to write a virus?
Not really. Who can stop you from writing one, and on what basis? However, the threat is that what starts in your computer as a challenge could easily leak out into the real world and cause nuisance for others. Once it leaks out, controlling it becomes significantly more difficult. Add to that the possibility of some other fellow programmer modifying your non-destructive code and making it a destructive variant. You will then probably be somewhat responsible morally and legally for the destruction caused. In conclusion, it will be far better to use your programming prowess in other areas where you could make a good name for yourself by building something of use for others.
Related
You might be interested in The History of Viruses or in the List of Computer Viruses.


Related Articles
No user responded in this post